Cloudflare not only provides CDN but also provides Firewall WAF for web application security. On the free plan, Cloudflare provides 5 firewall rules that are empty by default. You can more secure WordPress with Cloudflare using these five firewall rules.
Do you know, 6+ websites are hacked in 1 second. Most WordPress sites are hacked for weak passwords because hackers use the password generator to access wp sites.
For this, attackers try to log in on your site by accessing wp-login.php, wp-admin, xmlrpc.php and wp-comments-post.php etc.
You can check this activity using WordPress Security Plugins like the Sucuri scanner and other security plugins.
But, If you are using Cloudflare, you do not need any plugin, you can block attackers by enabling Cloudflare firewall rules.
Let’s start, here I explain a detailed guide on how to secure WordPress with Cloudflare firewall WAF.
Table of Contents
- How to Secure WordPress Using Cloudflare Firewall Rules (Step by Step Guide)
- 1. Block wp-login.php Attacks
- 2. Block xmlrpc.php Attacks
- 3. Protect wp-admin Area
- 4. Block No-referrer Request to Plugins
- 5. Reduce Spam by Blocking Direct Request to wp-comments-post.php
- Now, You Website is Slightly More Secure
- Bottom Lines,
How to Secure WordPress Using Cloudflare Firewall Rules (Step by Step Guide)
By following this guide, you can secure your site and block attacks before they even reach your web host server.
First Whitelist your IP Address:
Before you implement any firewall rules, you need first to do Whitelist your own IP address. After enabling firewall rules, you no need to pass them.
For this, go to your Cloudflare dashboard and click on the Firewall tab, then tools and enter your IPv4 or IPv6 address. After that, choose the whitelist in the drop-down menu.
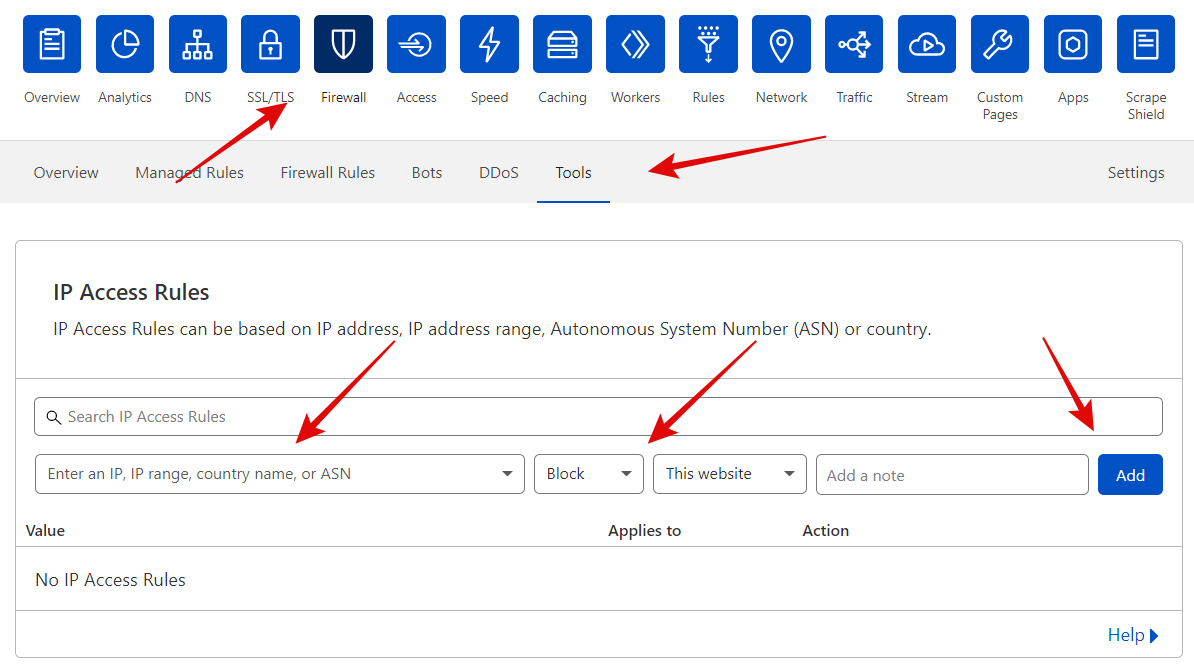
You can find your IP by searching “What is my IP” on google. If your IP changed in the future, you would need to re-enter it lest you get locked out of your WordPress admin area.
You can also block here any country in which you don’t want to access your website. Let’s start by enabling cf firewall rules.
1. Block wp-login.php Attacks
If you check your server logs and wp activity, you will probably find numerous IPs from all over the world trying to access your wp-config.php file.
This is the most common attack on WordPress installations. These are usually automated scans that do not pose a big threat, but you can block them for more security.
In your Cloudflare dashboard, click the Firewall tab then Firewall rules and press the Create a Firewall Rule button.
Now name it whatever you can like and fill it in by the below steps.
- Field: URI Path
- Operator: contains
- Value: /wp-login.php
[Action: Block]
If you did it right, you should see the following in the Expression Preview section.
(http.request.uri.path contains "/wp-login.php")
Save the rule, and it should be enabled automatically. After that, Cloudflare will start blocking every attempt to connect to wp-login.php.
These brute attempts will vanish from your server logs. Now you will track them on Cloudflare’s Firewall events section and verify that protection is working.
2. Block xmlrpc.php Attacks
After the wp-config.php attacks, xmlrpc.php second most common attack target. XL-RPC has legitimate uses, such as blogging from a smartphone or posting content to multiple WordPress sites at once.
If you do not need it, then you can be safely blocked it.
Creating a firewall rule for this, follow the same procedure as previously guide.
- Field: URI Path
- Operator: contains
- Value: /xmlrpc.php
[Action: Block]
After creating this correct rule, you can see this line in the Expression Preview section.
(http.request.uri.path contains "/xmlrpc.php")
Save rule, after that Cloudflare, will start to protect the XML-RPC attacks. Now, no one accesses your site xml-rpc.php file.
3. Protect wp-admin Area
Let’s do something that only you can access the admin area of your site. This rule is more complex than previously because now you need to add three exceptions.
First /wp-admin/ to protect WordPress admin area from attacks and hackers to access it.
Second /wp-admin/admin-ajax.php, which is used by certain plugins to display dynamic content on your website. After blocking /wp-admin/ it should be accessible.
Third /wp-admin/theme-editor.php runs an error check whenever you edit your theme through the build-in editor by creating a loopback request.
Go ahead and create the following rule:
- Field: URI Path
- Operator: contains
- Value: /wp-admin/
[AND]
- Field: URI Path
- Operator: does not contain
- Value: /wp-admin/admin-ajax.php
[AND]
- Field: URI Path
- Operator: does not contains
- Value: /wp-admin/theme-editor.php
[Action: Block]
Or you can also click on Edit expression and copy-paste in the following lines code.
(http.request.uri.path contains "/wp-admin/" and not http.request.uri.path contains "/wp-admin/admin-ajax.php" and not http.request.uri.path contains "/wp-admin/theme-editor.php")
After pasting the code, the firewall rule creates automatically. Now you will need to save the rule.
4. Block No-referrer Request to Plugins
After a weak password, most WordPress sites get hacked through insecure plugins. So the best thing, of course, is not to install them and always use up-to-date plugins.
If you used any plugin that did not get an update from a long time, you could use this firewall rule to block direct access to /wp-content/plugins/.
We need to prevent only the plugin folder, not the plugin script or CSS. So we will need to allow page requests and allow known good bots, crawlers like Google, Bing, Yahoo etc.
Create the following rule:
- Field: URI Path
- Operator: contains
- Value: /wp-content/plugins/
[AND]
- Field: Referer
- Operator: does not contains
- Value: yoursite.com (replace it with your real domain)
[AND]
- Field: Known bots
- Operator: equals
- Value: Off
[Action: Block]
Or, paste this expression indirectly (remember to replace yoursite.com with your domain):
(http.request.uri.path contains "/wp-content/plugins/" and not http.referer contains "yoursite.com" and not cf.client.bot)
After pasting the code, click on Deploy to automatically creating the rule and save it.
5. Reduce Spam by Blocking Direct Request to wp-comments-post.php
If your wp website received many spam comments, you could stop them by creating this Cloudflare firewall rule. This rule will make minimal spam and block spambots.
Create the rule as follows:
- Field: URI Path
- Operator: equals
- Value: /wp-comments-post.php
[AND]
- Field: Request Method
- Operator: equals
- Value: POST
[AND]
- Field: Referer
- Operator: equals
- Value: yoursite.com (replace with your domain)
[Action: Block]
Or, paste this expression directly in (remember to replace yoursite.com with your domain):
(http.request.uri.path eq "/wp-comments-post.php" and http.request.method eq "POST" and not http.referer contains "yoursite.com")
Remember, replace yoursite.com URL with your domain before saving the rule.
Now, You Website is Slightly More Secure
Congratulations! your WordPress blog is now more secure. These five Cloudflare firewall rules should cover the most common WordPress attacks.
Most attacks that you see in your server log or via a security plugin. Now you see all of them in the Cloudflare firewall section that is protected by the above rules.
When someone tries to access your admin area, they will be greeted with an “Error 1020” page like this. (you can confirm this by accessing it via a proxy or VPN):
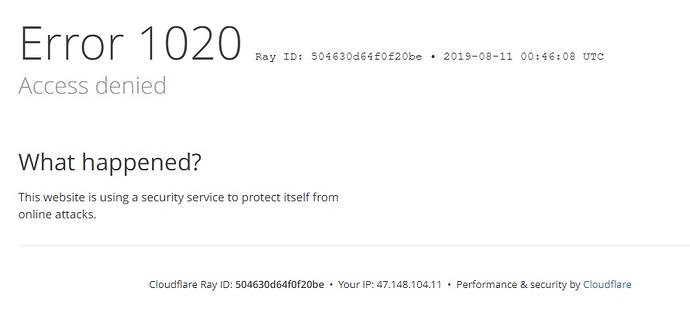
You can also add many other firewall rules as you needed, but there is only five firewall rule allow in the free plan. That means you will need to upgrade plan pro or higher to get more firewall rules.
Bottom Lines,
Cloudflare is the biggest Firewall & CDN provider globally, and millions of websites or blogs used it. But get the full benefit of this. You need setup it properly.
The above five firewall rules were empty by default. Now you can make secure WordPress with Cloudflare by enabling the above firewall rules.
Otherwise, you faced many issues. If you set up Cloudflare correctly, then it gives you good results. If you do not know the setup, I suggest Sucuri, where you do not need a manual setup.
But I love Cloudflare and always use it. I will explain more in the future about it another setup. Please share this tutorial with other bloggers.


Thanks for the great article. I am using Cloudflare since many days without firewall rules. But after reading your article I set up these rules and fortunately found many blocking reports that were trying to hotlink and access resources. Looking for more Cloudflare settings like this. Thanks again.
Dear Jumedeen khan,
I have problems with other web pages make hot-linking to my photos. So I will like to make a Firewall Rules, so it is not possible to do hot-linking to my photos, all jpg files! BUT the Firewall Rules needs to allow Search engines like google and yahoo (all the good bots) to index my photos!
I have been struggling with that problem for more than 3 months now and will be more than HAPPY if it something you can help with!!
Yes, we can do it via cloudflare firewall rules, I will explain it in my next article.
Dear Jumedeen Khan,
Thanks for your reply, I will look forward to a solution.
Hope it will be early Christmas
after using Protect wp-admin Area & Block wp-login.php Attacks firewall rules everyone access WordPress login page.
but is there any way to allow access which IP I whitelisted?
You can add challenge for login page by same rule.